Estimated read time: 9 minutes
What is end-to-end encryption?
End-to-end encryption (E2EE) is a secure communication method where only the sender and recipient can read the contents of the sent message. The message is encrypted on the sender’s device using a public key, and only the intended message recipient has the decryption key to decipher the encrypted message.
Not even the internet service provider or the messaging app can decrypt the encrypted content, even if it’s stored on their servers. The message data remains encrypted while being transmitted over the internet or any other network, protecting it from unauthorized third-party access.
End-to-end encryption is often used by messaging apps, email services, and other communication platforms to protect private information such as financial data, personal identification, and private communications. Encryption keys are generated and stored locally on the sender and recipient’s devices, making it difficult for potential attackers to steal the data.
How does end-to-end encryption work?
End-to-end encryption uses complex mathematical algorithms to encrypt plain text into ciphertext, ensuring that only the intended recipients can decrypt it. Encryption and decryption happen at the device level, so malicious actors won’t be able to access the transmitted data.
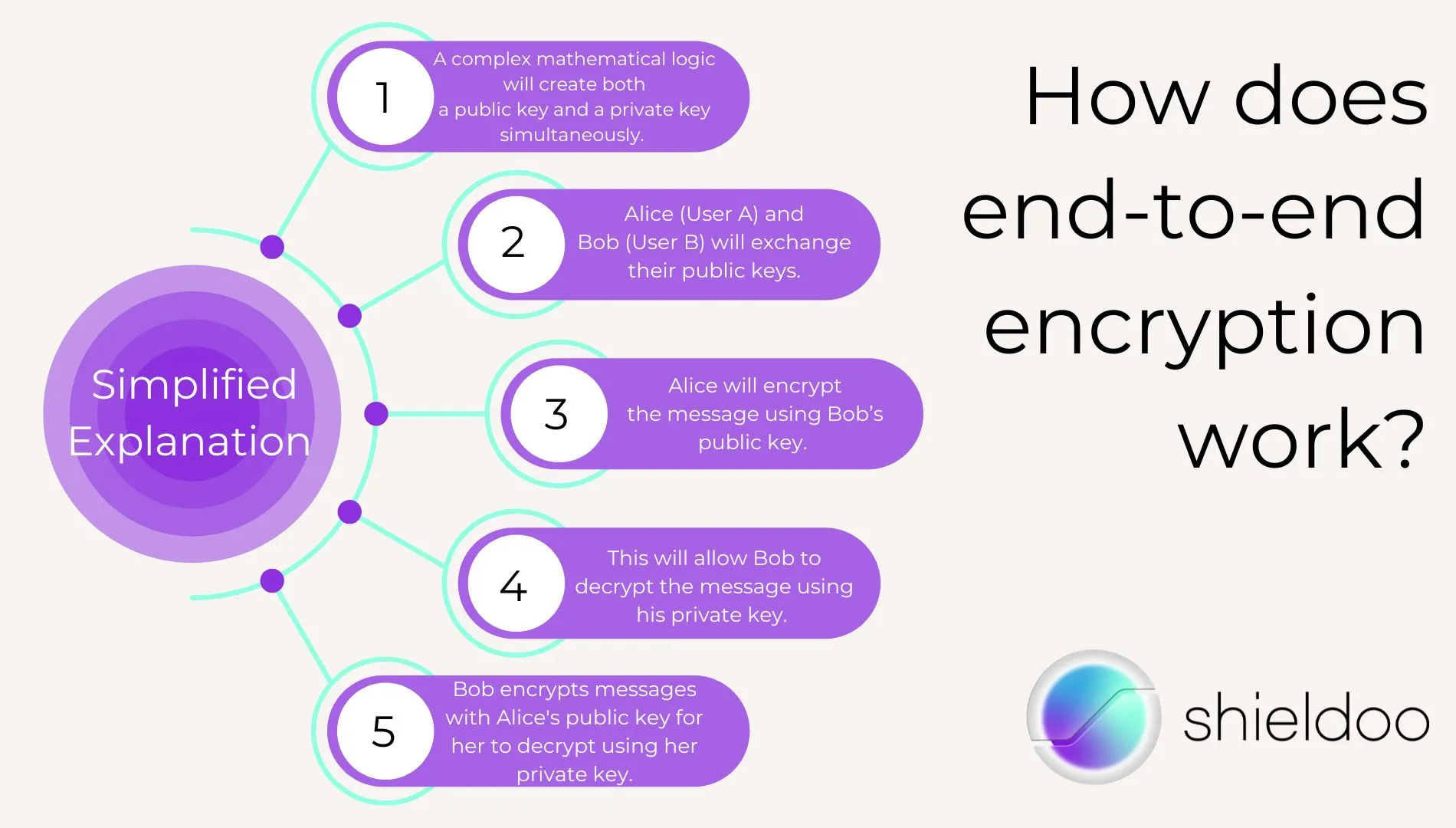
Here’s a simplified explanation of how it works:
- A complex mathematical logic will create both a public key and a private key simultaneously.
- Alice (User A) and Bob (User B) will exchange their public keys.
- Alice will encrypt the message using Bob’s public key.
- This will allow Bob to decrypt the message using his private key.
- When it’s Bob’s turn to send a message to Alice, Bob will encrypt the message using Alice’s public key so Alice can decrypt it using her private key.
This security method ensures that even if the message is intercepted by a third party, it cannot be read without the secret key. The end-to-end encryption system ensures that only the intended recipient can read the message.
What makes E2EE different from P2PE?

End-to-end encryption (E2EE) and point-to-point encryption (P2PE) are both security measures that protect data in transit. However, they differ in their scope and implementation of security protocols.
An E2EE message is encrypted at the sender’s device and decrypted at the receiver’s device. A P2PE message is encrypted at the sender’s device but decrypted at the application’s server. With E2EE, the message is encrypted the entire way, unlike P2PE, where message is decrypted in the middle.
With P2PE, the service provider can read the message and use it to send targeted advertisements.
Key Management Facility
E2EE keys are generated and managed by communicating users, meaning the only person who can view the plain text message are the sender and intended recipient(s). Third-party service providers have no visibility on the encrypted data and won’t be able to decipher it even if they want to.
Other types of encryption often use a service provider to manage encryption keys.
Privacy
End-to-end encryption provides more privacy and security than other types of encryption. With E2EE, the content of the message or data is completely protected and cannot be accessed by anyone else, including the service provider or unauthorized third parties.
This is particularly important in enabling messaging apps and other communication platforms to share encrypted data users want to keep private.
Data Security
End-to-end encryption protects against man-in-the-middle attacks, where a third-party intercepts and alters the transmitted data. With end-to-end encryption, the data is encrypted on the sender's device and can only be decrypted by a cryptographic key on the recipient's device. Only the user with the corresponding private key can access the message making it virtually impossible for a third party to decrypt and alter the data.
Complex Encryption Algorithms
E2EE and P2PE can use the same complex encryption algorithms to protect data from unauthorized access and interception. But they will vary on their implementation details and specific requirements.
End-to-end encryption uses asymmetric-key encryption algorithms, such as RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography), to provide end-to-end protection for data. It always involves using separate cryptographic keys and complex mathematical algorithms to secure data completely.
P2PE uses a combination of asymmetric keys, symmetric-keys and public-key encryption algorithms, such as AES (Advanced Encryption Standard) and RSA, to protect sensitive data such as the transmission of credit card information from a point-of-sale (POS) device to a payment processor.
What doesn’t E2EE encryption protect against?
While end-to-end encryption (E2EE) provides high security and privacy for communications, there are still some things that E2EE does not protect against. Here are some examples:
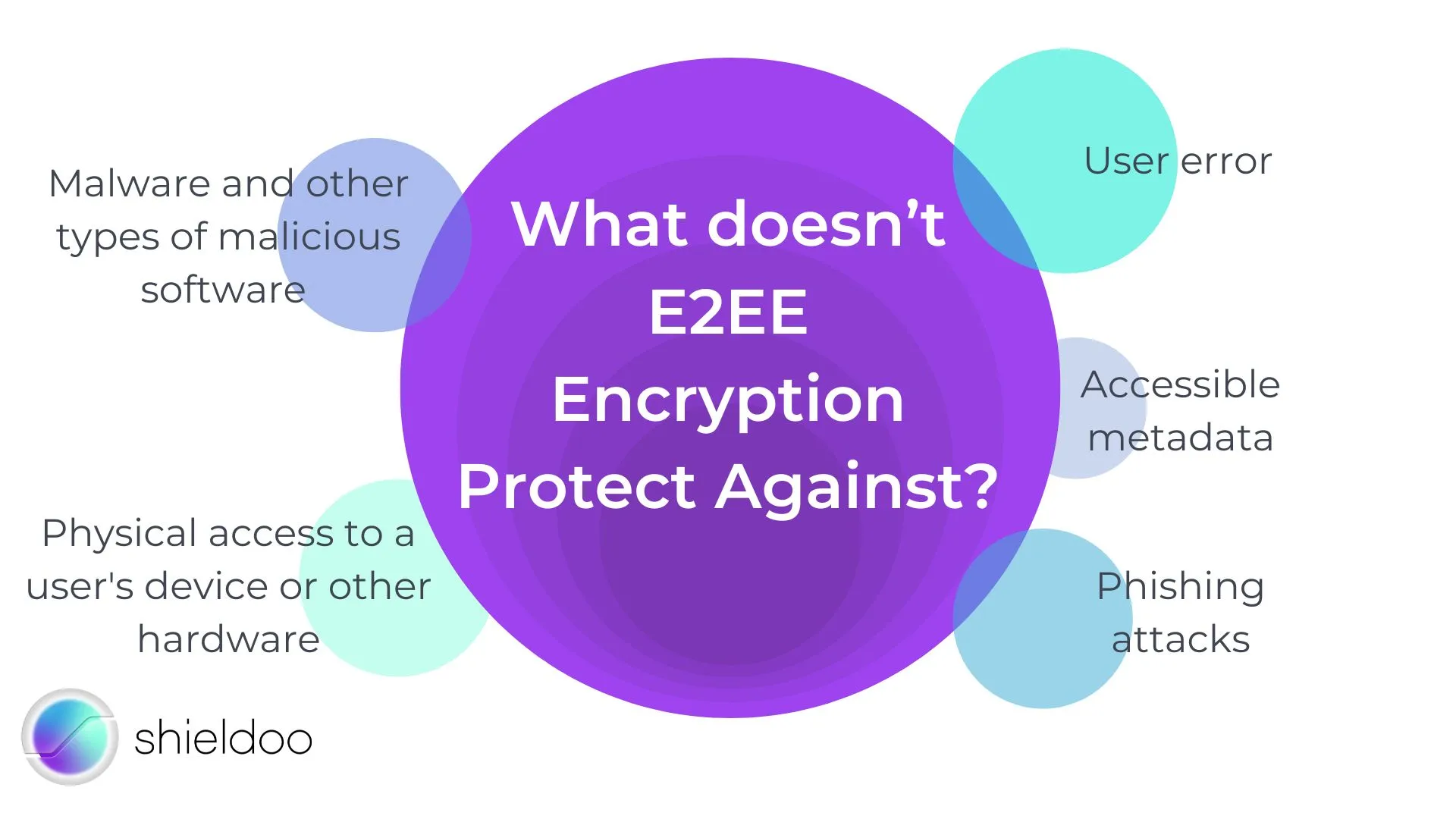
- Malware and other types of malicious software that infect a user's device and compromise their online privacy
- User error, such as accidentally sending sensitive information to the wrong person or storing data in an unsecured location
- Physical access to a user's device or other hardware, which lets an attacker bypass E2EE and access information
- Accessible metadata, such as time, date, and location of a message or call, and identity of the sender and receiver
- Phishing attacks where potential attackers trick users into divulging access to sensitive data
End-to-end encryption provides strong protection for the contents of a message or data during transmission, but it does not protect against all potential vulnerabilities and threats to a user's privacy and security.
Using best practices such as strong device and app passwords, common knowledge against malicious attacks, and security networks will further enhance the protection provided by end-to-end encryption systems.
What are the advantages of E2EE?
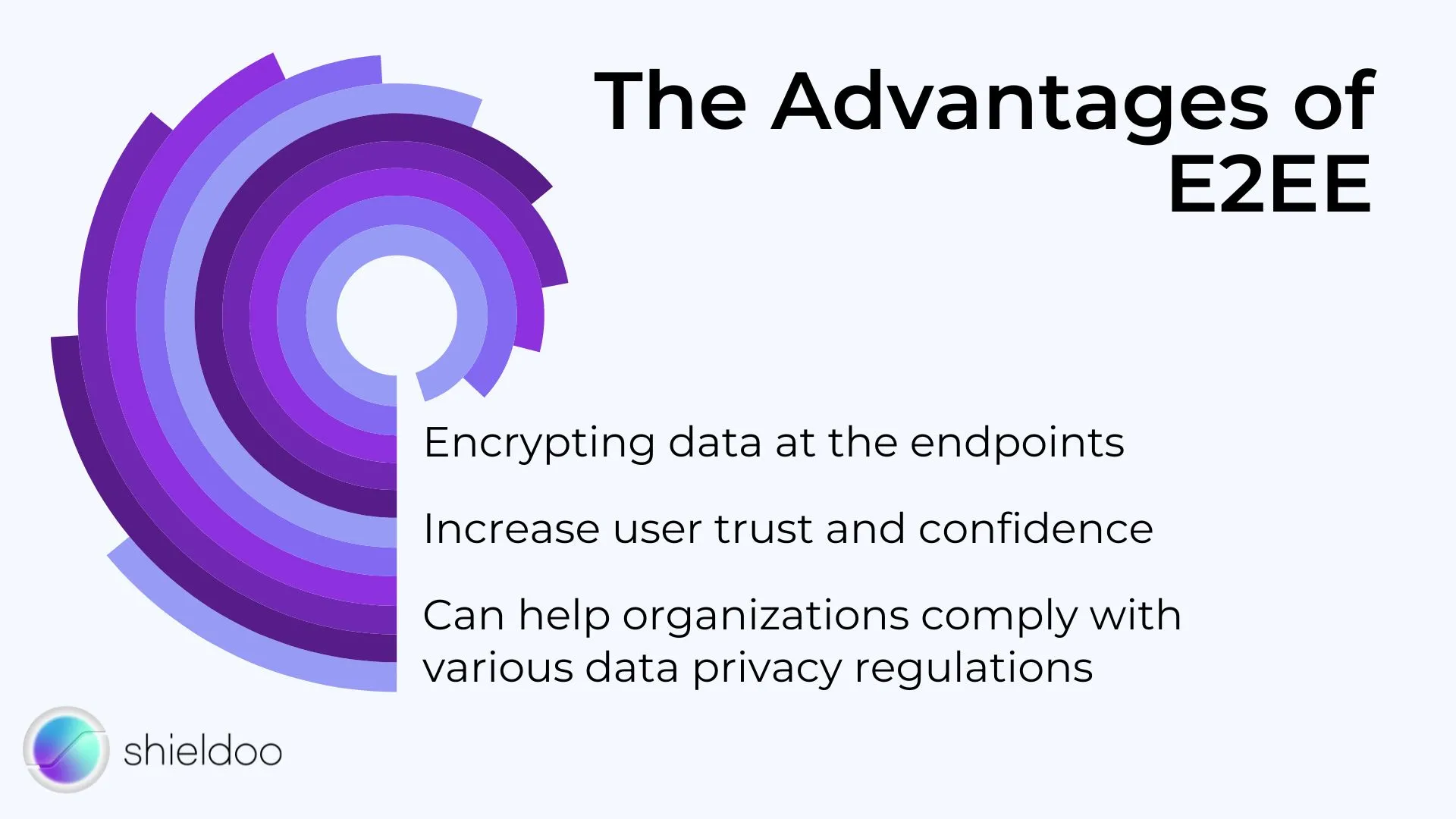
End-to-end encryption offers several advantages over other forms of encryption. By encrypting data at the endpoints, E2EE makes it difficult for hackers to access data and intercept sensitive information, enhancing data privacy protection. This can mitigate the risk of data breaches and leaks, which can have severe consequences for individuals and organizations.
End-to-end encryption can also increase user trust and confidence that they are the only ones with access to the plaintext version of their communication. This ensures the highest standards in data protection.
Another main advantage is that E2EE can help organizations comply with various data privacy regulations such as the GDPR in the European Union.
What are the disadvantages of E2EE?
Despite its advantages, end-to-end encryption has several drawbacks. One of the main disadvantages is the implementation complexity, requiring additional resources and expertise to ensure the encryption is done correctly. E2EE can also limit certain app or service functionalities, such as the ability to search or analyse messages, due to data encryption.
Additionally, there may be interoperability and support issues since different E2EE implementations may not be compatible with each other. End-to-end encryption can also require more storage and processing power, impacting performance and battery life, particularly on low-powered devices.
Another disadvantage of end-to-end encryption is the risk of lost data if users lose their encryption keys or forget their passwords. It can also make it difficult for law enforcement agencies to monitor or regulate content on messaging platforms, which may pose a challenge to maintaining public safety and preventing illegal activity.
How can Shieldoo help?

Shieldoo provides an encrypted tunnel between a user and the service or device the useris connecting to, providing better protection than a typical VPN. Traditional VPNs provide an encrypted tunnel between a user and a network or between two networks.
Shieldoo offers end-to-end encrypted communication between Shieldoo agents, ensuring the highest level of endpoint security and privacy for data communicated through the platform. Information sent via the platform is encrypted using a public key, and only people with corresponding decryption keys can decipher the messages.
FAQs
What is an example of end-to-end encryption?
Many messaging services implement end-to-end encryption. Some popular examples are WhatsApp, Telegram, Signal, and iMessage. These apps ensure that only the sender and recipient can view the plain text message and only transmit encrypted messages across their network. These apps also provide end-to-end encryption for voice and video calls.The healthcare industry also implements end-to-end encryption to protect sensitive patient information and comply with regulations surrounding the handling of private data. There are also backup and cloud storage services that provide end-to-end encryption to protect the stored data in their servers.
What does end-to-end encrypted mean?
End-to-end encryption protocol is a security protocol used to secure communication between two parties over a network. During E2EE, encryption and decryption are performed at the endpoints of the communication. The data remains encrypted throughout its journey between the two devices, and only the recipient with the decryption key can view the sent data. Even if a hacker or service provider intercepts the encrypted data during transmission, they cannot read or decipher it because it is encrypted.
Is end-to-end encryption unbreakable?
End-to-end encryption is considered very secure and one of the strongest forms of encryption currently available. However, it is not completely unbreakable.E2EE depends on the strength of the encryption algorithm, the length and complexity of the encryption keys, and the security of the devices and software used to encrypt and decrypt the data. If any of these factors are compromised, the security ofthe E2EE can be weakened or broken.
How encryption works step-by-step?
In general, encryption works this way: - Sender uses an encryption key to encrypt the plain text message. - Sender sends the encrypted data, or ciphertext, to the recipient. - Recipient receives the ciphertext and uses a decryption key to decrypt the data. - Recipient views the plain text.





