Estimated read time: 9 minutes
The workplace as we know it is changing before our very eyes. Technology itself is constantly evolving. The advent of remote work has prompted businesses to enable a remote access for employees. Unfortunately, these advancements have also fueled the development of more complex cyberattacks.

Nowadays, traditional network security measures just won’t cut it. While traditional firewalls can prevent threats from entering a network and disrupting internal services, they have some weaknesses. One such weakness is the number of devices that users themselves manage. If an individual user manages a device and is unable to secure it adequately from internal and external threats, this could render your entire system vulnerable to cyberattacks like phishing, data breaches, or ransomware.
The good news is cybersecurity is also evolving. New cybersecurity measures are being implemented to ensure that your networks are secure and protected, whether you’re accessing your system or applications remotely via the cloud or in person in the office.
One such network security measure is software-defined perimeters. In this article, we’ll take a closer look at SDPs and how they’re currently being used.
What Is Software-Defined Perimeter SDP?
A software-defined perimeter SDP is a modern approach to providing a secure access to your internal applications and network resources. It works by cloaking or hiding your internet-connected infrastructure, such as routers or servers, thus preventing external or unauthorized parties from accessing it.
Unlike traditional network security systems, which rely on protecting hardware from external threats, an Software Defined Perimeter solution establishes a security perimeter using software, which then regulates application access to your internal network and other sensitive resources based on identity. Thus, only users who have been verified and authorized may have a remote access to your infrastructure.
The great thing about an Software Defined Perimeter is that it’s easy to implement, and because it’s software, its deployment is agile. Furthermore, it offers security for your network regardless of where it’s hosted. Whether you’re using a cloud solution or a private corporate network, your infrastructure will still be protected.
Lastly, its network architecture is based on zero trust network access (ZTNA), which provides flexible ad customizable security policies. By leveraging a zero-trust approach, a software defined perimeter SDP is capable of consistent and continuous verification and validation of users and their devices. At the same time, all remote users’ traffic is fully audited.
Software Defined Perimeter Use Cases
Below are some of the top use cases for software defined perimeter solutions:

As a Virtual Private Network Replacement
Traditionally, when an organization needs to grant a user access to its internal resources to remote workers or third-party users, it would resort to using a virtual private networks (VPNs). While VPNs provide privacy and network security by encrypting your data, it does have some drawbacks.
- VPNs can be very hard to scale
If you have plenty of external users, then you may need to purchase a new VPN server to accommodate this surge. Unlike traditional virtual private networks VPNs, Shieldoo™️ is easily scalable because it leverages P2P connections, instead of routing traffic over one hop.
- It’s not always totally secure
VPNs aren’t impervious to brute force attacks and other password attacks, and they don’t offer much in the way of segmentation. This means that once an attacker has gained users access to your VPN by guessing the correct password, they’d have access to all your resources on that network.
Shieldoo™️ uses zero trust network access and follows “least privilege” principles. With Shieldoo™️, you and other users are granted application access only to the specific resources you need to access. Due to granular access control, security administrators can grant application access based on user identity , device state , user location and other custom security policies.
- It may affect your speed
Using VPNs can increase latency because your traffic will travel longer distances. This is because VPNs tend to route traffic to a hub instead of connecting it directly to the resource. Additionally, high traffic (SD-WAN, MPLS) can lead to higher operational costs.
- Issues with segmentation
In order for traditional VPNs to achieve reasonable network segmentation, you either have to create multiple networks or set up complex routing rules. Doing so only increases your network’s complexity, which, in turn, can make it more challenging to operate, manage, and secure.
As an Alternative to Traditional Static Network Segmentation
An software defined perimeter SDP can be used as a replacement for VPNs. Think of it as a “tunnel” that connects your home network to a security perimeter. An SDP is a robust security solution that can also be used within the established perimeter. With an SDP, there’s no need for you to establish static networks. Instead, you can move freely with ZTNA and create connections on an as-needed basis and only when you need to connect your devices.
For example, your IT helpdesk receives a ticket where it needs to fix a certain user’s computer. Once a helpdesk personnel accepts the ticket, the network connection will be opened via the SDP. Once the problem is solved, the connection is closed. This illustrates that access to the resources is given only when it’s needed, therefore effectively reducing a potential attacker’s lateral movement.
Other SDP Use Cases
SDPs are versatile and can be used to easily connect devices, networks, or users between multiple environments like multi-cloud or hybrid cloud environments. It can also be used to implement standardized network security measures across all your networks. Lastly, an SDP can be used to regulate third-party secure access to your resources, thus giving you improved segmentation.
Cloud Security Alliance about SDP
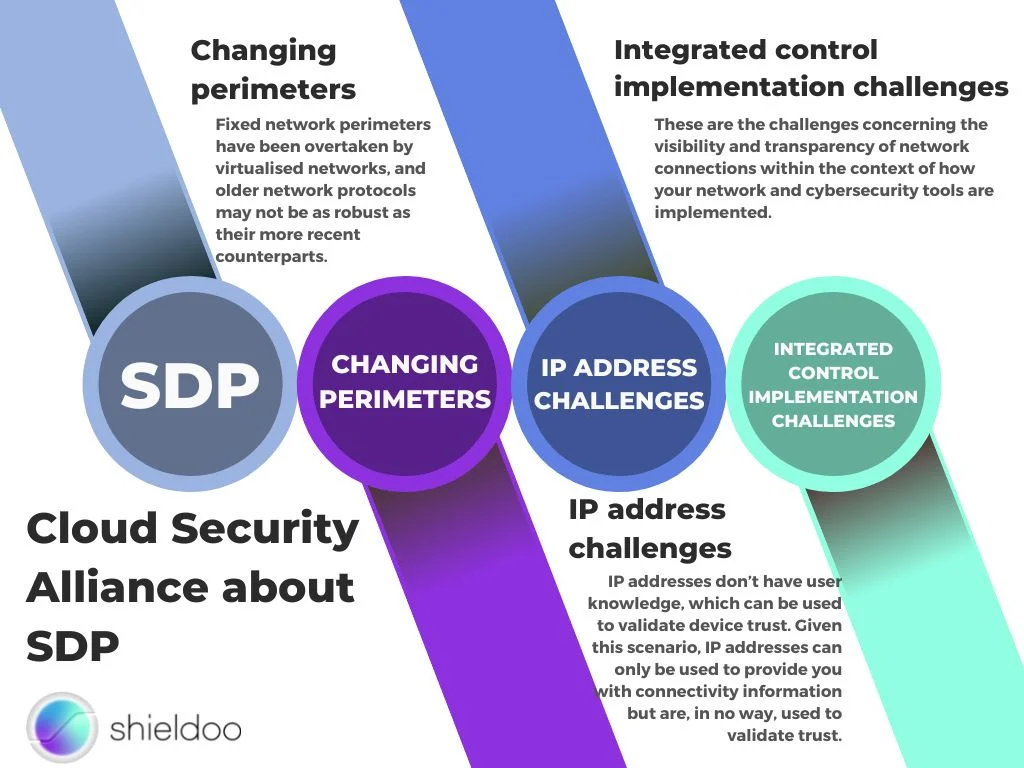
With the emergence of newer threats, there is a need to keep up with how we approach and implement network security. According to research by the Cloud Security Alliance, the leading organization dedicated to identifying best practices to create more secure cloud computing environments, there are particular issues that demand changes in how we implement network security, which include:
- Changing perimeters. Fixed network perimeters have been overtaken by virtualized networks, and older network protocols may not be as robust as their more recent counterparts.
- IP address challenges. IP addresses don’t have user knowledge, which can be used to validate device trust. Given this scenario, IP addresses can only be used to provide you with connectivity information but are, in no way, used to validate trust.
- Integrated control implementation challenges. These are the challenges concerning the visibility and transparency of network connections within the context of how your network and cybersecurity tools are implemented.
The research further highlights how existing zero trust users can benefit from a zero trust implementation using software-defined perimeters and why SDP, when used as a framework to implement zero trust strategies, can help prevent large-scale breaches.
The Cloud Security Alliance also emphasizes how zero trust implementation using SDP can help organizations defend their systems from newer variations of attack methods. By implementing SDP, you’re able to fortify your cloud computing security measures and your system’s security. It also makes it easier for you to adapt to newer, more complex attacks.
These findings and more can be found in CSA’s white paper.
Next-Gen Security with Shieldoo™️
Keep your systems secured with Shieldoo™️ secure network (mesh), a next-gen solution for cybersecurity that offers robust segmentation and scalability. The Shieldoo™️ secure network is designed to keep up with modern challenges and the hybrid workplace.
Make sure that your business is protected from internal and external threats. Try Shieldoo™️ now.
FAQs
Is SDP a VPN?
An SDP is an entirely different security solution from a virtual private network (VPN). VPNs earned a legacy for becoming an essential tool in establishing network security. However, as the Internet matures and threats to security increase, the limited features of a VPN are incapable of protecting sensitive data. An SDP is built on the Zero Trust principles, wherein no one inside or outside the network is trusted. Verification checks are performed before a user’s access request gets granted. SDPs reduce the risk of malicious activity by only granting minimal access to the application or data requested by the user. SDP overshadows VPN in terms of not only tighter security but also scalability. For VPNs to secure bigger networks, investing in more hardware is a must. SDPs on the other hand, enjoy flexible scaling across peer-to-peer and hybrid networks.
Is SDP a replacement of VPN?
An SDP is a modern-day solution to network security with an emphasis on granular security and remote access to resources on a given network. It’s meant to address the flaws of security solutions like VPNs. It will only be a matter of time until SDPs completely replace VPNs. VPN is highly dependent on forming secure connections in a given location. Meanwhile, location is irrelevant to SDPs. Verification checks are constantly performed regardless of the user’s position relative to the network they wish to connect to. Whereas a VPN grants access to a network and its applications, SDP trusts no user nor device. Every application is heavily secured, and users must request access and undergo verification for every resource they need. Such a level of security greatly reduces the risk of giving access to unwelcome users.
Is ZTNA and SDP the same?
Zero Trust Network Access (ZTNA) is a security solution that allows users remote, secure access to applications. It’s a subset of technologies following the Zero Trust Security Model, which adheres to the philosophy that without thorough verification, no one inside or outside the network is to be trusted. Users requesting access to an application shall only receive minimal access specifically for that application. Should they require access to another application on the network, they will have to go through another round of verification. ZTNA follows the Zero Trust Security Model in verifying users and granting independent access to applications on a given network. At its core is the trust broker, a technology that bridges the user and application with a thorough verification check of user identity, context, and security. Depending on how ZTNA is implemented, the trust broker is a set of technologies operated on a cloud-based provider or a network of computers. Technically, a software-defined solution (SDP) is one method for Zero Trust security to be implemented. Merchants can market ZTNA as a software solution in the form of SDPs. ZTNA and SDP are not entirely one and the same, but they are often used interchangeably.





