Estimated read time: 4 minutes
Today, I want to share key trends and challenges in the security area that are important to your company or business. Information is based on ENISA (The European Union Agency for Cybersecurity) reports and Check Point's Cyber Attack Trends reports.
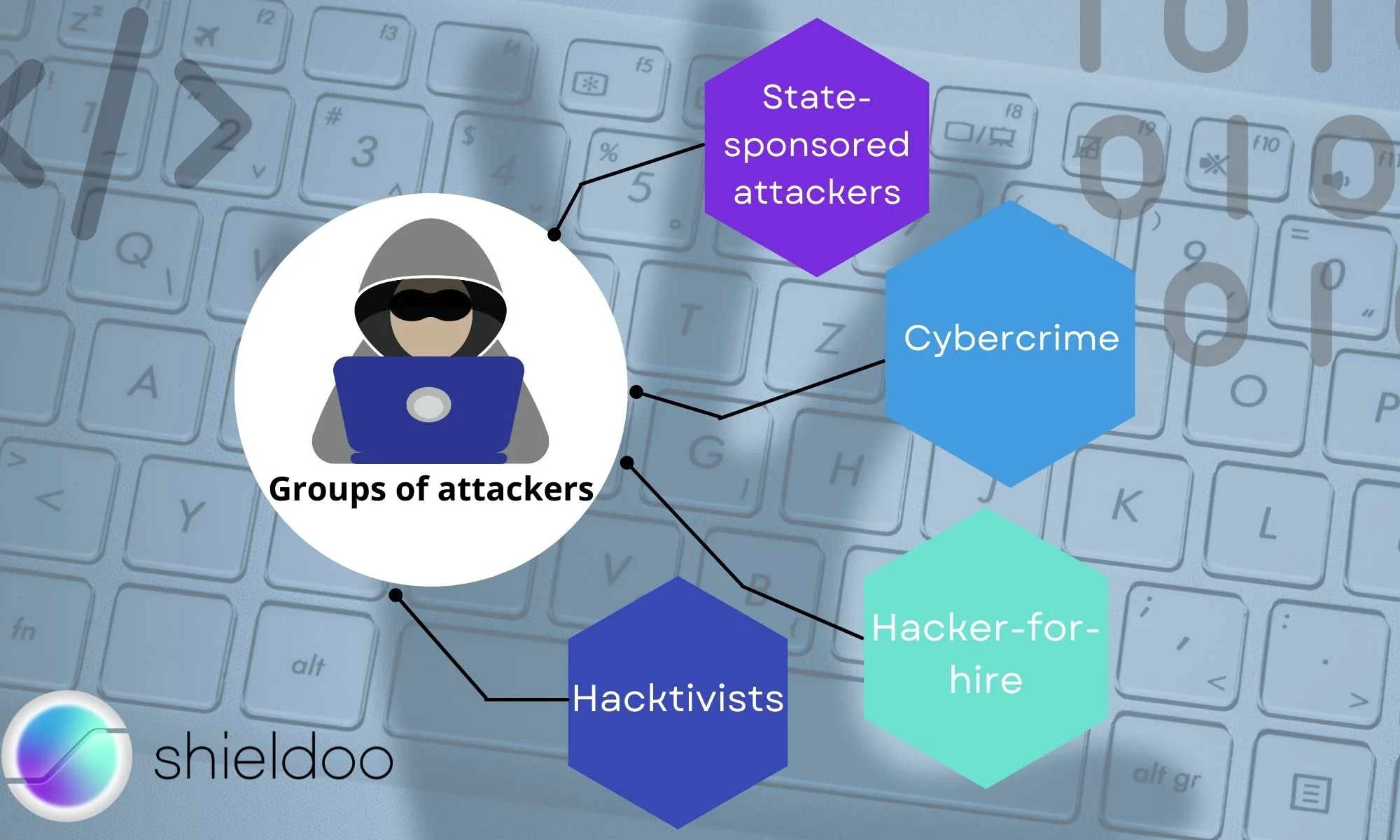
Let's start with categories of attackers; it means who is attacking companies in 2021, according to the ENISA report. There are four groups of attackers:
- State-sponsored attackers - politically driven activities
- Cybercrime - activities driven by organized crime groups
- Hacker-for-hire - organized group of hackers which can be hired as a service
- Hacktivists - but their operations remain low in numbers, sophistication, and impact
Few key trends in the cybersecurity area:
- Governments increased efforts to disrupt and take legal action against state-sponsored threat actors.
- Cybercriminals are increasingly motivated by the monetization of their activities. As a result, cryptocurrency remains the most common pay-out method for threat actors.
- The two most common ransomware infection vectors are compromised through phishing emails and brute-forcing on Remote Desktop Services.
- Malware targeting container environments have become much more dominant.
- The Phishing-as-a-Service business model is more popular.
- Artificial Intelligence enabled disinformation supports attackers in carrying out their attacks.
- The disinformation-as-a-Service business model has grown significantly, stimulated by the increasing impact of the COVID-19 pandemic and the need to have more information.
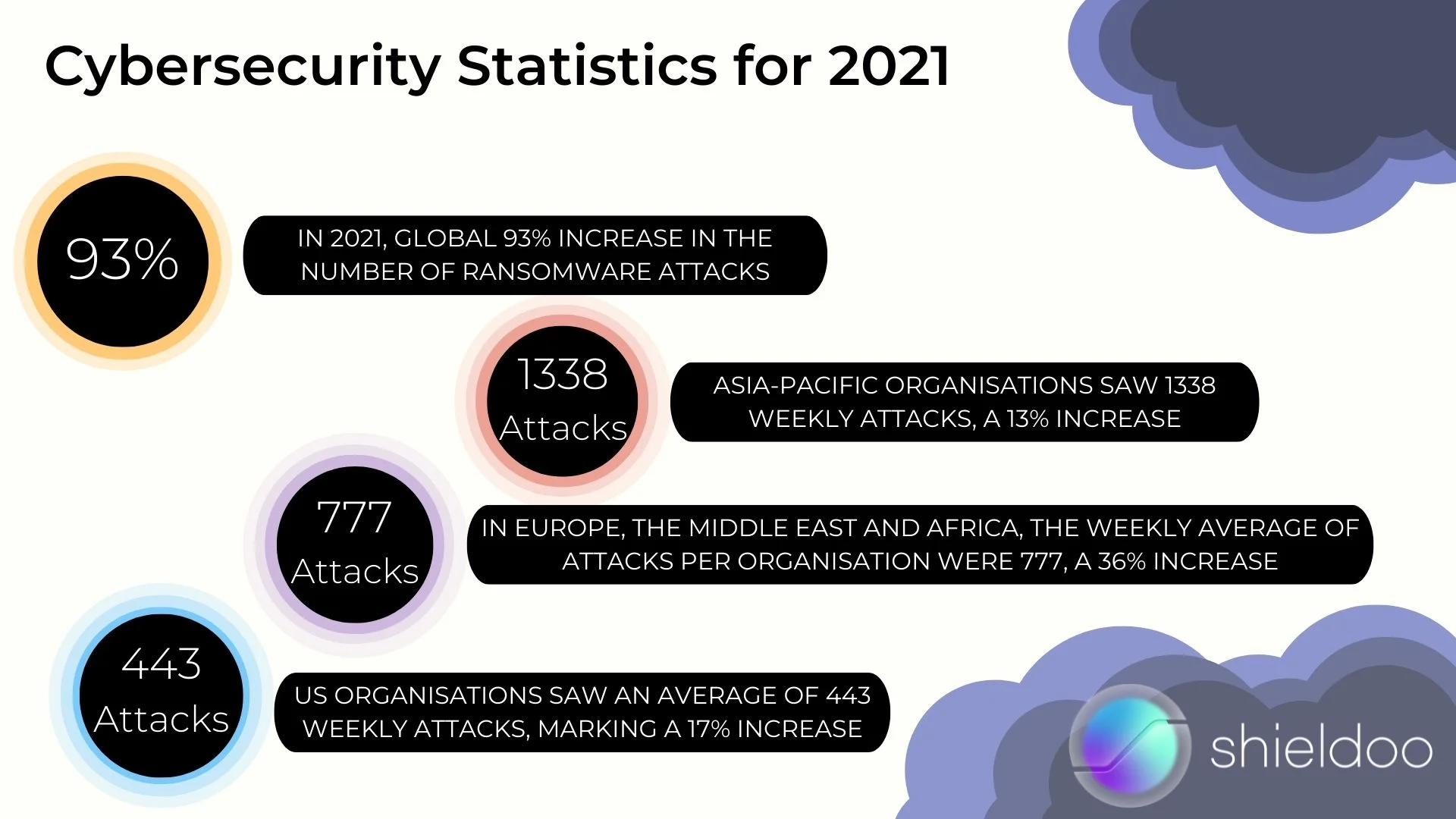
Cybersecurity Statistics for 2021
In 2021, we can see a dramatic global 93% increase in the number of ransomware attacks. US organizations saw an average of 443 weekly attacks, marking a 17% increase. In Europe, the Middle East and Africa, the weekly average of attacks per organization were 777, a 36% increase. Finally, Asia-Pacific organizations saw 1338 weekly attacks, a 13% increase.
Ransomware actors adopted a new strategy in 2021. In addition to stealing sensitive data from organizations and threatening to release it publicly, attackers now target organizations' customers and business partners and demand payment from them.
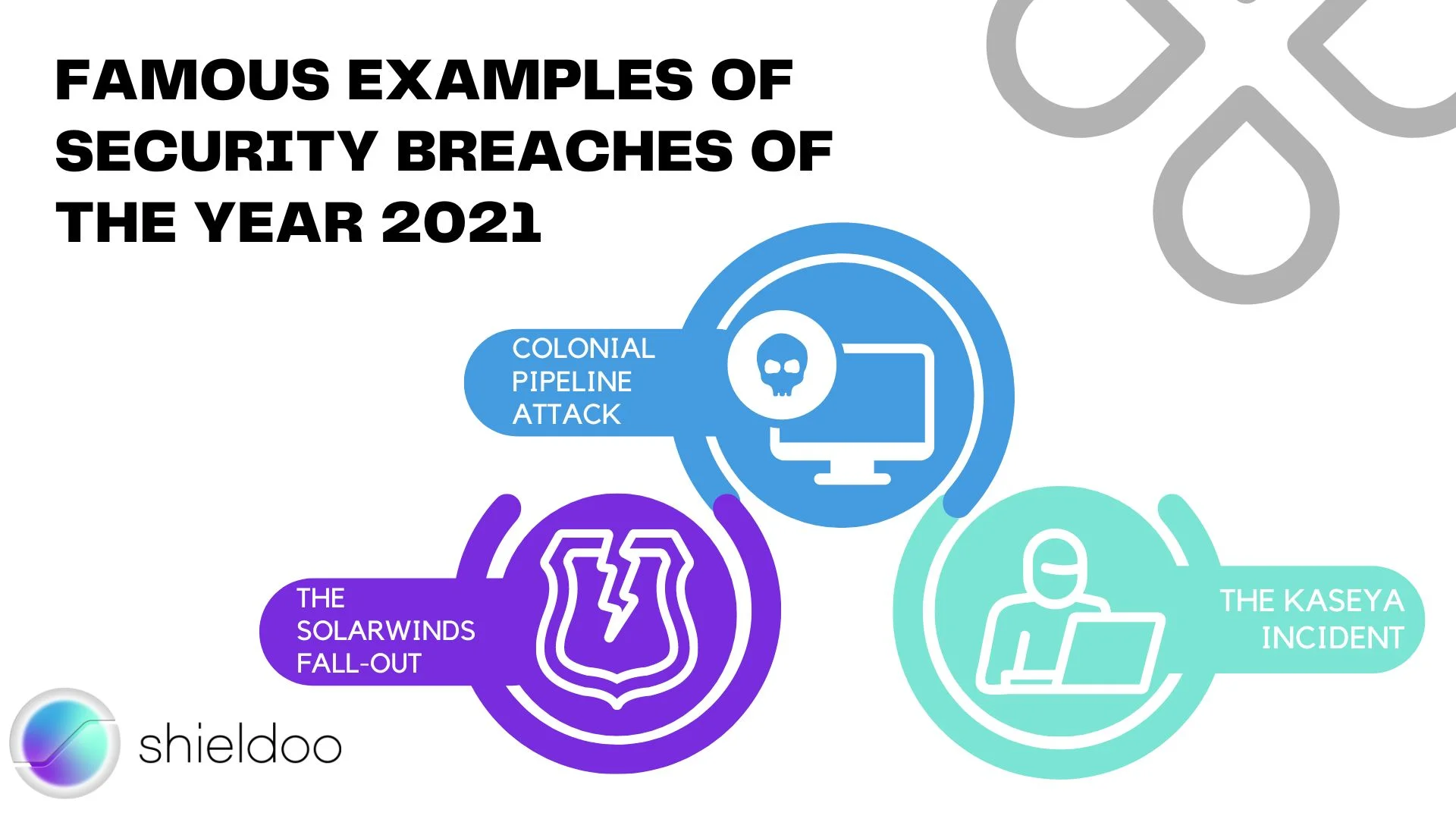
There are three famous examples of security breaches of the year 2021:
THE SOLARWINDS FALL-OUT
More than 18,000 companies and government offices downloaded what seemed to be a regular software update on their computers, but it was a Trojan. In this way, an attacker can use prepared backdoors to access organizations' assets.
COLONIAL PIPELINE ATTACK
In May 2021, a major US fuel company fell victim to a ransomware attack which led to its entire fuel distribution pipeline being shut down.
THE KASEYA INCIDENT
The attack occurred over the US Independence Day weekend on IT management software firm, Kaseya, and combined supply-chain and ransomware exploits.
And now three examples from the networking security area:
Draytek is a Taiwan-based manufacturer of networking equipment and management systems such as firewall, VPN devices, and routers. In January 2020, one router product line was found to be vulnerable to a critical vulnerability that allows an unauthenticated attacker to execute attackers' code in devices. This year, it was one of the most heavily leveraged vulnerabilities by cyber attackers.
Next one:
F5's BIG-IP is a popular multi-purpose networking security device. However, in May 2021, a critical flaw was discovered in BIG-IP's management interface. Various attackers quickly adapted bot networks by integrating malware into the botnet and start scanning the internet for vulnerable devices.
And the last one:
The University of Hertfordshire, UK, suffered an attack that shut down its IT systems including Office 365, Teams and Zoom, local network, Wi-Fi, email, data storage, and VPN. Following the attack, all live online teaching was cancelled for two days.

Try Shieldoo™️
Be careful, don't underestimate security in your cloud solutions. Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is a cyberattack?
Cyberattack may be defined as any malicious offensive assault targeted against computer network, information system, infrastructure or personal device. It may be attempt by an individual or an organization.
How to prevent cyberattacks?
It is necessary to try to reduce risk by following steps: secure hardware, protect and encrypt data, use security software, educate employees, promote a security-focused culture,...
What are cyber security solutions?
Cyber security solutions consists of tools and softwares that help protect organizations against cyber attacks. It may prevent application downtime, theft of sensitive data, damage to reputation, etc.





